PowershellMonitor
monit powershell behaviour by hooking powershell script engine.
- detect obfuscated script
- log powershell behaviour use lua
- intercept behaviour by lua(by return non zero)
- win7 x86 x64 powershell 2.0
- win10 x86 x64 powershell 5.1
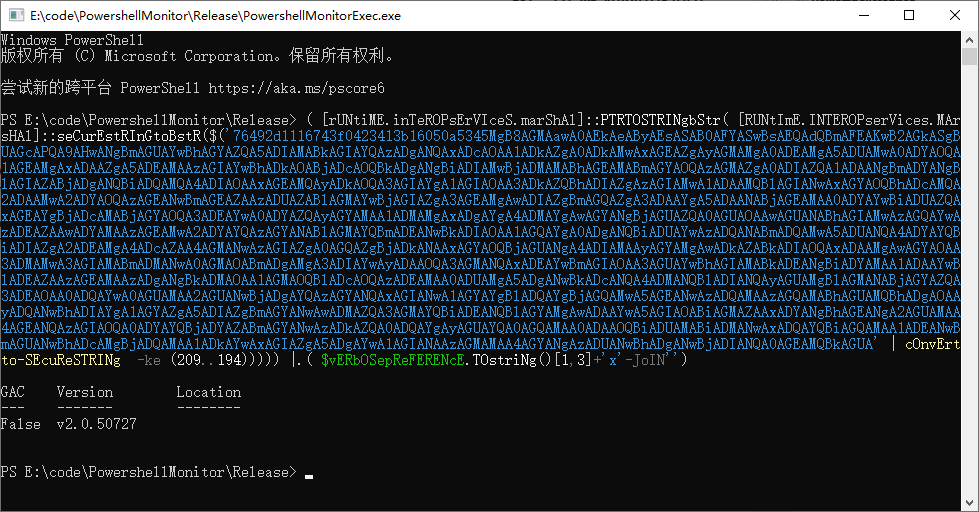
- Execute powershellexec.exe, it will start a powershell process and inject powershellmonitor.dll(or powershellmoniter64.dll) into the process, then use this powershell session execute poweshell command, the behavior(format to json struct) of the powershellscript will be pass to the luascript(luascript.lua) , then according to your lua script, you can log the behavior
- VirtualAlloc
- VirtualAllocEx
- WriteProcessMemory
- CreateRemoteThread
- CreateThread
- DownloadString
- DownloadFile
- DownloadData
- UploadData
- UploadString
- UploadFile
- Shell.Application.Open
- WScript.Shell.Exec
- WScript.ShellRegDelete
- WScript.ShellRegWrite
- CallByname
- Assembly Load
- OpenRead(url)
- Invoke-Expression
- Invoke-WebRequest
--[[
powershell json define:
functionname
argcount
arg1
arg2
arg3
arg4
arg5
arg6
arg7
---]]
function powershellcheck(jsonstring)
local params = cjson.decode(jsonstring)
local funcname = params.functionname
local logpath = "e:\\code\\PowershellMonitor\\Release\\log.dat"
local binarypath = "e:\\code\\PowershellMonitor\\Release\\binary.dat"
local scriptpath = "e:\\code\\PowershellMonitor\\Release\\script.dat"
if funcname == 'downloadstring' or funcname == 'openread' then
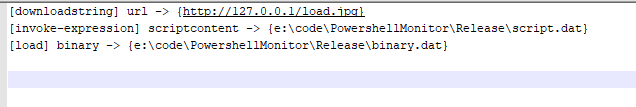
Log.write(logpath, string.format('[%s] url -> {%s}', funcname, params.arg1))
return 0
elseif funcname == 'invoke-expression' then
Log.write(scriptpath, params.arg1)
Log.write(logpath, string.format('[%s] scriptcontent -> {%s}', funcname, scriptpath))
return 0
elseif funcname == 'load' then
Log.writebinary(binarypath, params.arg1)
Log.write(logpath, string.format('[%s] binary -> {%s}', funcname, binarypath))
return 0
elseif funcname == 'virtualalloc' or funcname == 'virtualallocex' or funcname == 'virtualprotect' then
Log.write(logpath, string.format('[%s] notify -> {native api called}', funcname))
return 1
end
return 0
end